In brief:
- With GenAI-powered chatbots expanding the scope and scale of cybersecurity attacks, cybercrime has emerged as the #1 business risk.
- Top network infrastructure security best practices to protect your business include implementing Zero Trust Architecture, Identity and Access Management, patch management, strong detection and contention tools, employee security training, and more.
- Automation plays a critical role in threat detection, executing repetitive tasks, and responding to low-level incidents – enabling security teams to focus on critical infrastructure issues.
- Handling evolving threats to IT infrastructure and security requires an effective provider who can deliver a 24×7, proactive, multi-layered security framework harnessing best-of-breed tools, strong processes, and qualified resources.
Cybercrime emerged as the top business risk confronting enterprises worldwide in 2024 – surpassing labor shortages, business disruptions, and regulatory changes. Implementing IT infrastructure security best practices is key for data protection within your enterprise as the sophistication of cyber threats increases and new vulnerabilities cause attack surfaces to widen.
Businesses are facing cyberattacks at an alarming rate – the third quarter of 2024 saw the average number of weekly attacks per organization climb to an all-time high of nearly 1,900, according to Check Point’s “2025 Cyber Security Predictions.” That’s a staggering 75% increase from the same period in 2023.
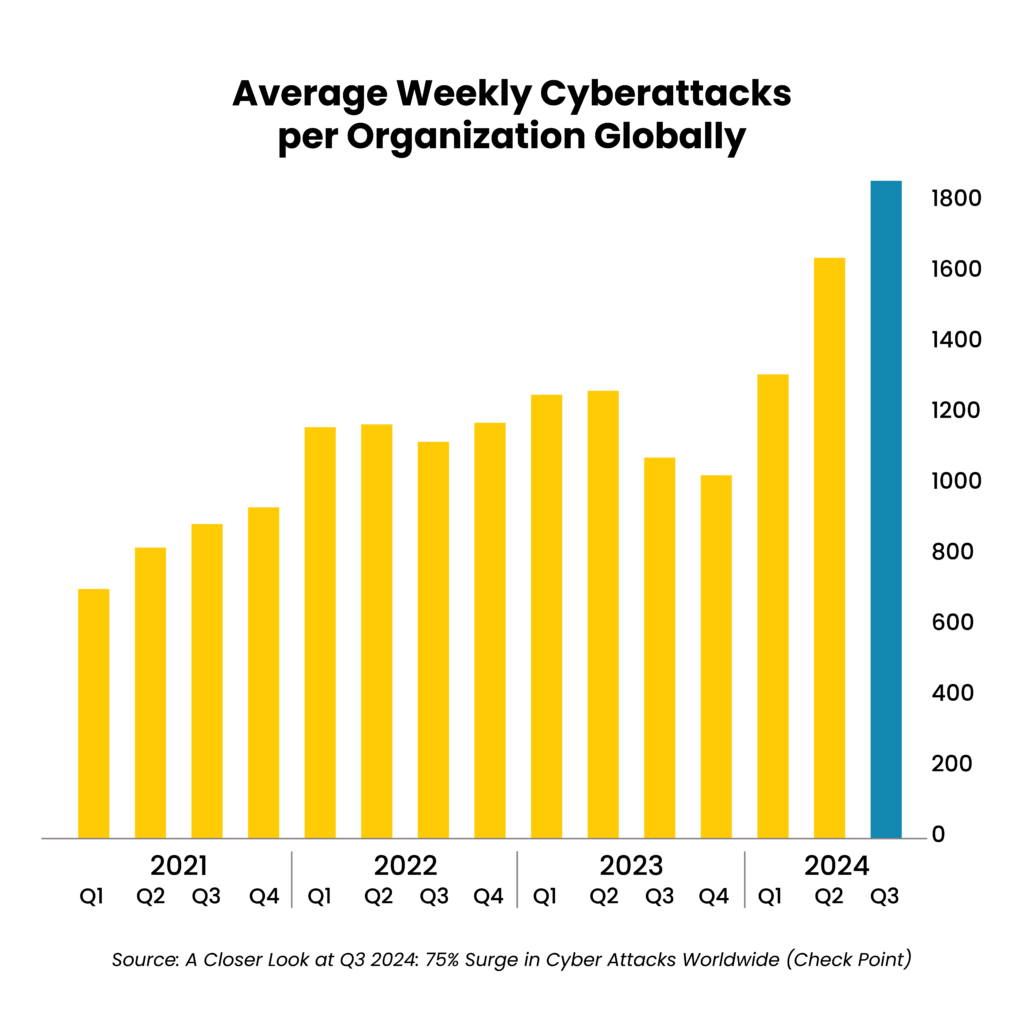
As technology continues to advance, the number of risks is expected to keep increasing. This blog details 12 essential IT cybersecurity best practices every organization should follow to detect and block malicious attacks and safeguard sensitive data.
What are the main security challenges for today’s IT infrastructure?
Rapid adoption of OpenAI’s large language model (LLM) chatbot, ChatGPT, broke new ground for AI – and also dramatically altered the cyber threat landscape. Cybercriminals now employ LLM chatbots to launch highly targeted phishing attacks at an alarming scale.
OpenAI said in its October report that it regularly stops deceptive networks from using its LLM for malicious purposes as cybercriminals leverage ChatGPT to write code, develop malware, conduct social engineering attacks, and carry out post-compromise operations.
Data breaches triggered by employees unintentionally sharing sensitive information with ChatGPT, Google Gemini, or similar models are an equally grave concern – constituting one of the biggest security risks in 2025, according to Check Point’s report.
Rapid cloud adoption, remote workforces, and the increasingly interconnected nature of systems have also created new entry points for cybercriminals to exploit – further causing complexity and risk to spiral.
Top threats include ransomware and double-extortion attacks, insider threats, credential theft and phishing, third-party and supply chain vulnerabilities, and more. Worse, cybercrime is getting more expensive – the average cost of a data breach for U.S. organizations today is $9.36 million – higher than any other country (IBM 2024 Cost of a Data Breach Report).
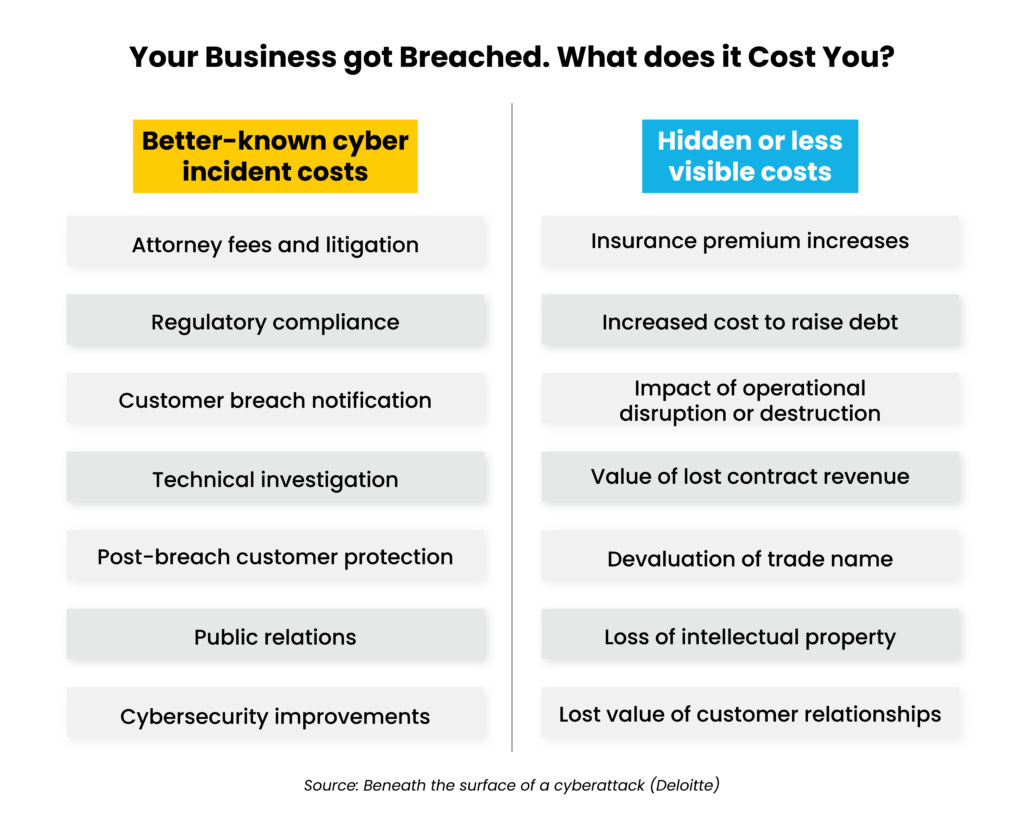
12 infrastructure security best practices every business should follow
Modern IT infrastructure includes on-premise servers, cloud services, networks, storage, and endpoints like laptops and mobile devices. It also incorporates virtualization, data management systems, and communication tools to support business operations and collaboration.
Given this vast network of interconnected components, best practices for securing infrastructure cover a wide range of strategies.
1. Zero Trust Architecture
Zero Trust Architecture (ZTA) is a cybersecurity model that aims to reduce the risk of data breaches by assuming no user or device can be trusted. It follows the principle of least privilege, which means users and devices are only granted permissions they need to do their jobs.
ZTA uses several security technologies to enforce access policies, including multi-factor authentication (MFA), micro-segmentation (dividing a network into segments at the application layer to increase security), and real-time monitoring.
2. Strong Identity and Access Management (IAM)
Multi-factor authentication is a key component of IAM, especially for privileged (administrator) accounts with extensive network access and permissions. These accounts are attractive targets for attackers as they offer the ability to access, modify, or manage critical resources.
IAM also involves adoption and use of password-less authentication methods, as well as Privileged Access Management solutions that control and audit usage of administrator accounts.
3. Consistent patch management and system updates
Patching is a fundamental security practice for fixing known software vulnerabilities, preventing hackers from exploiting these entry points to gain unauthorized access to systems and data. Ransomware attacks stemming from unpatched vulnerabilities show the greatest business impact, leading to four times higher recovery costs of $3 million and recovery time of a month or more, Sophos’ “2024 Unpatched Vulnerabilities” report states.
Maintaining a regular patch management schedule combined with prompt system updates effectively minimizes cyber risk by shrinking the attack surface and staying ahead of threats.
4. Network segmentation and monitoring
Network segmentation effectively limits the spread of malicious activity within IT network infrastructure by dividing it into smaller, isolated segments. This prevents attackers from easily moving laterally across a system, minimizing potential damage from a breach.
Simultaneously monitoring these segments further enables early detection of suspicious activity and rapid response to potential threats. Intrusion Detection Systems (IDS) are key to analyzing traffic and providing alerts when suspicious activity is detected. IDS should be placed at critical points in the network architecture, including the perimeter, data centers, and high-value segments – with thresholds set carefully to reduce false positives without missing critical alerts.
A CIO’s Guide to Harnessing Next-Gen Monitoring to Reduce Cloud Costs and Risks

The result: better containment of breaches, improved visibility, reduced entry points, simplified troubleshooting, and increased compliance.
5. Centralized Security Information and Event Management (SIEM) solution
SIEM forms the backbone of effective security monitoring. It collects and aggregates log data from across your IT network infrastructure, helping security teams identify and respond to potential threats in real time. Key components include:
- Centralizing log collection from all systems and applications, including network devices, servers, and endpoints.
- Clear definition of alerts based on threat intelligence and historical data, focusing on high-impact events like unauthorized access or unusual data transfers.
- Automated response for low-level incidents, allowing security teams to focus on critical issues.
6. Endpoint and extended security solutions
Endpoint and extended security solutions help organizations rapidly detect and respond to threats at the device level, before attacks can cause significant damage. Endpoint Detection and Response (EDR) solutions use advanced analytics, machine learning, and automation to detect threats and monitor endpoints for malicious activity. Extended Detection and Response (XDR) solutions monitor networks, applications, and the cloud. Both work with other security solutions such as firewalls, Virtual Private Networks (VPNs), and intrusion detection systems to provide comprehensive detection.
7. Security operations with playbooks and SOAR solutions
SOAR (Security Orchestration, Automation, and Response) solutions enable security teams to integrate and coordinate separate security tools like SIEM and EDR, automate repetitive tasks, and streamline incident and threat response workflows. Response playbooks, which outline procedures for responding to security incidents and threats, help reduce human error by standardizing and automating responses to common incidents.
Together, these solutions significantly improve the speed and efficiency of incident response, allowing security analysts to focus on more complex investigations and prioritize threats effectively. By reducing the time taken to detect and remediate security incidents, potential damage can be minimized.
But keep this in mind: regular review of playbooks based on incident post-mortems and lessons learned is critical to improve future responses.
8. Strong vulnerability and risk management program
A strong vulnerability and risk management program supports an organization’s security posture by proactively identifying, assessing, and addressing potential system vulnerabilities. This enables timely remediation that minimizes the likelihood of cyberattacks and data breaches, protecting sensitive information before malicious users can slip through.
9. Securing cloud infrastructure access
Cloud infrastructure security is table stakes today as cloud technology underpins much of the digital operations of modern enterprises. Protecting data, applications, and systems stored within the cloud is vital to ensuring the confidentiality, integrity, and availability of critical information while minimizing the risk of financial loss and reputational damage to an organization hit by a data breach.
Cloud Security Posture Management (CSPM) solutions continuously monitor cloud configurations for compliance with security best practices, enforcing strong policies through Identity & Access Management, periodic access reviews for cloud resources, and more.
10. Continuous end-user security awareness training
Even the best IT security infrastructure can be compromised by human error. According to IBM’s report, phishing emails that trick employees to click on malicious links or provide sensitive data are the most common cyberattacks, costing organizations an average of $4.88 million.
The #1 factor for reducing those costs: employee training, the report found.
Regular training fosters a culture of security by educating staff at every level about common risks, best practices, and the proper response to suspicious activity. Best practices include conducting regular phishing simulations to identify gaps in awareness, segregating and customizing training based on roles, and regularly updating training content as new threats emerge.
11. Test and update your incident response plan regularly
Make sure your incident response plan remains effective and relevant for guiding your organization through IT security incidents. This includes:
- Simulated tabletop exercises at least once per year, where participants discuss how they would respond to an emergency to test the plan and identify improvement opportunities.
- Clear assignment of roles to ensure team members understand their responsibilities during an incident.
- Post-incident reviews to identify gaps and update the plan accordingly.
12. Maintain comprehensive documentation and reporting
Clear documentation and reporting of incidents helps teams manage security tasks effectively while providing valuable data for audits, compliance, and post-incident reviews. Every incident should be documented thoroughly, including a detailed timeline and response steps. Generating monthly or quarterly security summaries is also key to effective governance and compliance, helping management understand your organization’s risk profile.
Why Auxis: The right IT infrastructure security partner
Infrastructure security monitoring and management require a proactive, multi-layered approach to safeguard against evolving threats. However, most organizations find it too expensive and resource-intensive to maintain a Security Operations Center (SOC) capable of ensuring comprehensive 24×7 security monitoring and management.
Just the infrastructure costs for setting up an in-house SOC for a 5,000-strong organization can approach $1.1 million, according to a Kobalt.io estimate. Additional operational, staffing, and training costs can run well over a million more – as surging demand for a limited pool of cybersecurity talent enables resources to command some of the highest salary brackets in IT.
With nearshore delivery of IT security services, Auxis helps organizations solve these challenges – offering the real-time collaboration and highly skilled, certified talent needed to address urgent security threats quickly and cost-effectively. Auxis also brings the flexibility to deploy best-of-breed security tools through its partnerships with top providers, manage clients’ existing security tools, or use a hybrid approach – all layered with a best-in-class security framework that ensures regulatory compliance.
From standing up a turnkey SOC to 24/7 threat detection and response, Auxis is the right partner to shield your digital assets against the growing landscape of cyber threats – allowing you to grow your business with confidence.
Want to learn more about how IT infrastructure security solutions can benefit your organization? Schedule a consultation with our IT infrastructure security experts today! You can also visit our resource center for more IT security tips, strategies, and success stories.