In brief:
- Cybersecurity remains the top business risk for enterprises worldwide in 2025.
- AI has shifted the cyberthreat landscape into overdrive, with 97% of organizations concerned their organization will suffer an AI-generated cybersecurity incident.
- A cybersecurity roadmap outlines the strategy for achieving your organization’s security goals, assessing its readiness, and ensuring continuous improvement.
- Five essential steps to building an effective IT security roadmap include conducting a cybersecurity assessment, determining critical goals, creating an action plan, and more.
Cybersecurity stands as the top business risk for enterprises worldwide for the fourth year in a row – eclipsing challenges like supply chain disruptions and macroeconomic developments by a higher margin than ever before, states the 2025 Allianz Risk Barometer. In this climate, building an effective cybersecurity roadmap is vital to protecting your organization from the growing sophistication of cyberthreats and their increasing financial and operational impact.
The average global cost of a data breach reached a record high of $4.88 million in 2024, IBM’s Cost of a Data Breach Report found. In the U.S., costs were nearly double at a staggering $9.36 million – the highest of any country.
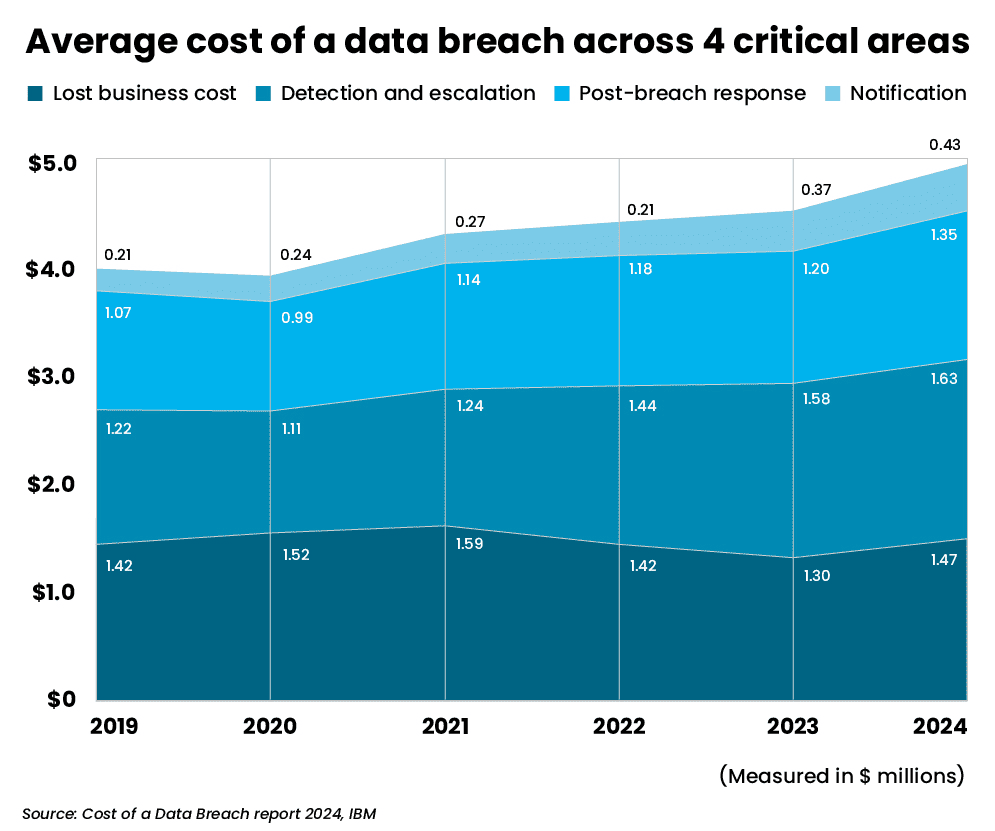
So, what’s changed? Rapid advances in AI are a significant factor. Utilizing advanced models, AI expanded the landscape of cyberthreats to include newer and more impactful types of attacks (deepfakes, AI-powered social engineering, etc.) while bringing down the cost of executing sophisticated attacks by as much as 95%.
Some 75% of security professionals said they had to change their cybersecurity strategy in the last year due to the rise in AI-powered cyberthreats, while 97% are concerned their organization will suffer an AI-generated cybersecurity incident, Deep Instinct’s 2024 report found.
For many cybersecurity experts, these alarming statistics indicate that cyberattacks are no longer just a possibility, but an inevitable event waiting to happen to businesses - irrespective of size or industry. To defend and recover from such attacks with minimal impact and in the shortest possible time span, you must continuously assess your security posture, identify areas for improvement, and implement security controls and processes to mitigate risks.
This blog lays out the five critical steps for building an effective roadmap for cybersecurity – defining what an IT security roadmap is, the benefits of having one for your organization, and how to get it right.
What is a cybersecurity roadmap?
A cybersecurity maturity roadmap is a comprehensive framework that outlines a proactive approach for achieving your cybersecurity goals and objectives, mitigating risks, complying with industry regulations, and protecting your assets and sensitive data.
To ensure a comprehensive and structured approach, your cybersecurity maturity roadmap should include the following components:
Rethinking Corporate IT Guide: 5 Simple Strategies for Transforming IT into a Business Enablement Powerhouse

- Current security posture assessment: This assessment evaluates the organization’s existing cybersecurity measures and practices to identify vulnerabilities and strengths.
- Security maturity level target: Clearly define cybersecurity goals aligned with the organization’s risk tolerance and business objectives. These must be specific, measurable, and time-bound.
- Gap analysis: The gap analysis identifies the difference between the organization’s current security posture and its target security maturity level.
- Framework selection: Adopting a well-chosen cybersecurity framework, such as NIST or ISO 27001, can provide a valuable starting point for measuring and improving your organization’s cybersecurity maturity. It aligns your initiatives with recognized security best practices and potentially relevant regulations.
- Action plan and timeline: The action plan outlines steps that need to be taken to achieve the organization’s target security maturity level, with milestones and timelines for each phase.
- Budget and resource allocation: Identify budget, personnel, and technology to achieve the targeted security maturity level, allocated based on priority and criticality.
- Communication plan: Developing a communication plan keeps all relevant internal and external stakeholders informed of the cybersecurity maturity roadmap’s progress. It also establishes protocols for reporting and addressing security incidents.
Getting buy-in for these initiatives from executive leadership is an essential prerequisite for cultivating cybersecurity maturity and implementing the roadmap effectively. Communicating the benefits of cybersecurity maturity to leadership is key, showing them how investing in protection can improve the organization’s bottom line.
Measuring the success of roadmap initiatives is also essential to demonstrating value and identifying areas where additional investments may be needed.
Benefits of a roadmap for cybersecurity
There are many benefits to creating a roadmap for improving your organization’s cybersecurity.
- It helps your organization identify, prioritize, and address your cybersecurity concerns. This assists in optimizing resource allocation and ensuring that security investments are focused where they are most needed.
- It provides a framework for developing and implementing security controls and measures for incident response and recovery, ensuring organizations are well-prepared to handle and recover from cybersecurity incidents.
- It helps track the maturity of the organization’s cybersecurity program over time and helps make necessary adjustments.
- It facilitates communication and collaboration between stakeholders, employees, and partners, fostering awareness about the importance of cybersecurity and their roles in maintaining it.
- It helps comply with industry-specific regulations, aligning the organization’s cybersecurity practices with regulatory standards as well as protecting your customers’ data and trust.

5 steps for creating an IT security roadmap
A mature cybersecurity posture makes for a more secure business, making your organization more attractive to clients, investors, and partners. Follow our 5-step roadmap to strengthen your security stance in today’s fast-changing environment:
1. Conduct a cybersecurity assessment
This is the first and most important step in creating a roadmap. The assessment should be conducted by a team of cybersecurity professionals or an experienced third-party vendor and should include a thorough evaluation of the organization’s current cybersecurity posture, including its risks, strengths, and weaknesses.
It should focus on key areas such as endpoint and network security, identity and access management, data protection, application security, and incident response. Physical security, governance, and compliance, as well as mobile and cloud security, should also be considered.
The assessment should identify any regulatory or compliance requirements that the organization must meet, and the cybersecurity framework to be adopted. The outcome of the assessment should be a comprehensive report that includes recommendations for improving the organization’s cybersecurity posture.
2. Set goals and objectives
Once the assessment is complete, and the organization identifies the gaps between the current level of its cybersecurity maturity and where it aims to be, the next step is to set goals and objectives, (i.e., the targeted maturity level).
The goals set should be specific, measurable, attainable, relevant, and time-bound (SMART). Some examples of SMART goals:
- implementing multi-factor authentication (MFA) for all user accounts by the end of Q3.
- achieving a 20% improvement in employee awareness of phishing threats through training sessions within six months.
- establishing a Security Operations Center (SOC) and hiring qualified personnel within six months.
Your goals should also include achieving compliance with security frameworks and industry-specific standards and regulations in a timely manner, such as PCI DSS for implementing secure coding practices for all e-commerce applications and HIPAA (Health Insurance Portability And Accountability) for enhanced data encryption protocols for healthcare providers.
Common metrics that demonstrate the value of these initiatives to leadership include number of security incidents, blocked attacks, the time it takes to detect and respond to security incidents, and the cost of security incidents.
The goal-setting process should involve a wide range of leadership across the C-suite, IT, business operations, security and risk management, legal and compliance teams, communication/public relations specialists, and more. This ensures comprehensive coverage, collaboration, and alignment with organizational objectives.
3. Develop an action plan
Once goals and objectives have been established, the next step is to develop a plan to achieve them, including:
- Specific actions and timelines for applying new security controls, such as implementing assets like firewalls and updated security software, training employees on cybersecurity best practices, etc.
- A budget for the implementation of new security controls and technologies.
- Measures for monitoring and evaluating the effectiveness of new security controls and technologies. These can vary across organizations depending on industry and company size.
4. Put your plan into action
Implementation is the next step, putting your action plan and new security controls in place. It is important to track the progress of the plan and make any necessary adjustments. For this, a governance body needs to overlook the implementation of the devised plan. The governance body should include:
- Board members
- C-level executives including the chief information security officer
- A Security Steering Committee with representatives from across departments
The implementation phase should also include regular testing and validation of the security controls and technologies to ensure they are working as intended.
5. Regular reviews and assessments
This is essential to measure the success of the action plan and its implementation in the real world – enabling you to adapt and improve security measures, ensure ongoing effectiveness, and boost resilience against emerging cyber-risks. The review assessments should include penetration testing, vulnerability assessments, and compliance audits. Third-party penetration testing, which involves hiring an external firm to simulate cyberattacks, is key to validating the security of operating systems and should be performed annually.
Implementing a cyber security roadmap is incomplete without cultivating a culture of cybersecurity in the long term. A strong cybersecurity culture is essential for improving your level of security maturity – making employees aware of the importance of cybersecurity, fostering a sense of responsibility, and reducing incidents of employees unknowingly enabling hackers.
Why Auxis: The right IT security partner
Putting together and implementing a cybersecurity roadmap can be daunting and expensive. Gartner expects a 15% increase in security software spending in 2025 alone, triggered by the adoption of AI and GenAI.
An effective roadmap also requires specialized expertise and skills that are often not readily available in-house, particularly at a time when cybersecurity talent commands one of the highest salary brackets in IT.
The number of organizations facing a critical lack of skilled security workers is growing, with 53% reporting security skills shortage in 2024 versus 42% the year before, IBM found. Even worse, the report highlights a strong link between the worsening skills shortage and higher data breach costs.
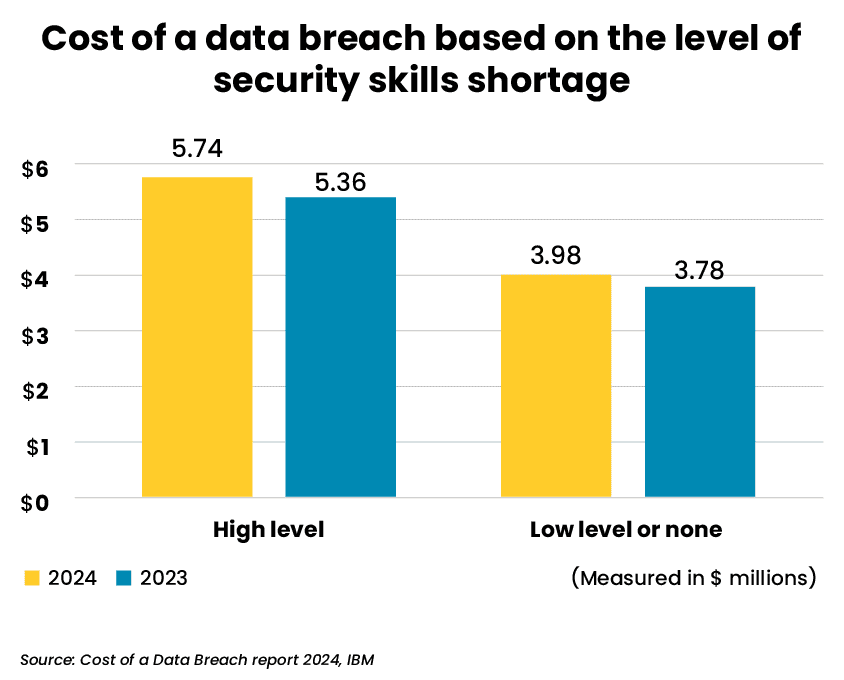
Partnering with a quality Managed Security Services Provider (MSSP) like Auxis offers specialized expertise, continuous monitoring, and access to advanced technologies in a cost-effective manner, allowing organizations to enhance their security posture effectively while not losing focus on their core operations.
From helping you understand the vulnerabilities in your security posture to building and implementing an effective IT security roadmap, Auxis is the right partner to shield your organization against the growing landscape of cyberthreats, allowing you to grow your business with confidence.
Want to learn more about how to build an effective IT security posture? Schedule a consultation with our cybersecurity experts today! You can also visit our resource center for more IT security tips, strategies, and success stories.
Frequently Asked Questions
What is a roadmap for cybersecurity?
+A cybersecurity roadmap is a strategic plan that outlines the steps an organization must take to strengthen its security posture over time. It includes key initiatives such as risk assessments, policy development, technology implementations, and employee training.
What role does artificial intelligence play in modern cybersecurity?
+Artificial intelligence enhances an organization's cybersecurity posture by enabling real-time threat detection, automated response, and predictive analytics. AI-driven tools can analyze vast amounts of data to identify anomalies, detect malware, and prevent attacks before they escalate. Machine learning models continuously adapt to evolving threats, improving security posture over time. By integrating AI, organizations can strengthen defenses, reduce response times, and enhance overall security.
What are the common challenges faced while implementing a cybersecurity roadmap?
+Common changes while implementing an IT security roadmap include budget constraints, lack of essential skills, and resistance to change. Organizations often struggle with integrating new security technologies into existing systems without disrupting operations. Keeping up with evolving threats and regulatory requirements also adds complexity to execution.
Partnering with an experienced managed security services provider can be beneficial for overcoming such challenges and ensuring expert guidance, addressing skills gaps, gaining access to advanced security tools, and continuous threat monitoring. Gaining executive buy-in and ongoing employee training are also essential for overcoming organizational obstacles.
How can I assess my organization's current cybersecurity posture?
+Assessing your organization's cybersecurity posture requires a comprehensive evaluation of existing security measures, risk assessment, vulnerability testing, as well as reviewing policies, controls, and technologies to identify gaps and potential threats. An experienced and proven implementation partner can be vital to the process. Schedule a consultation today with our cybersecurity experts to learn how we can help identify and remedy gaps.