In recent years, the number of cyber-attacks has risen dramatically, and big and small businesses are facing an expanding threat landscape. 83% of organizations surveyed in IBM’s Cost of a Data Breach Report said they had experienced more than one breach. The average cost of a data breach touched a record high of $4.35 million in 2022, the report also found.
The types of cyberattacks have also diversified, with ransomware attacks evolving into double and triple extortion attacks which apply further pressure on victims via DDoS attacks and/or threatening to leak their clients’ data.
Traditional perimeter-based security models, which focus on securing the boundaries of a network using firewalls, intrusion detection systems (IDS), and virtual private networks (VPNs), are no longer enough to protect against these threats. As a result, many organizations are turning to a new security paradigm: Zero Trust.
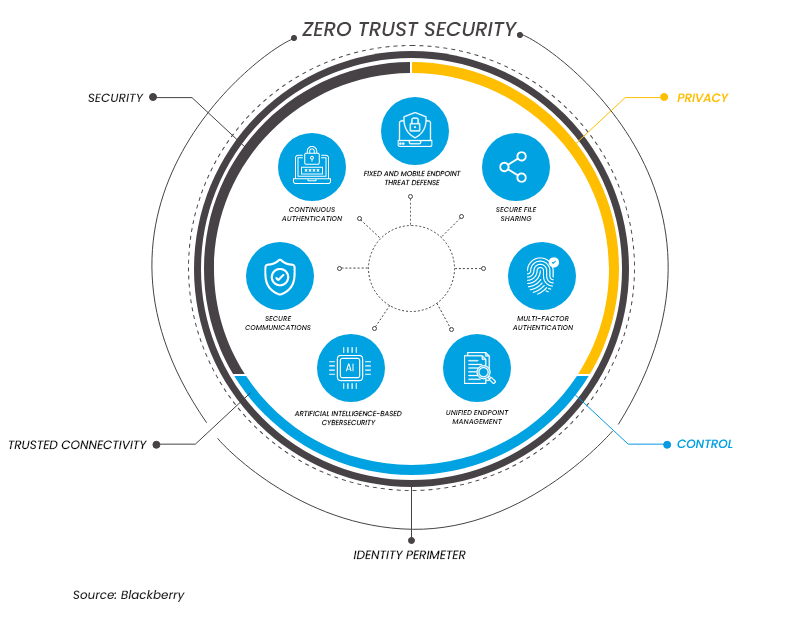
The Zero Trust security model is a “never trust, always verify” approach that assumes no user or device should be automatically trusted, even if they are within the network perimeter. It requires continuous verification and authorization of user identity and devices attempting to access network resources.
Zero Trust leverages powerful identity services to secure access to apps and infrastructure for every user and helps organizations mitigate the potential impact of a security breach.
The five main principles or pillars of the Zero Trust model are:
1. Verify Explicitly
Zero Trust requires that the identity of users and devices be verified explicitly before granting them access to network resources. Traditional username and password authentication is no longer sufficient in today’s threat landscape. Instead, for a higher level of security, organizations should implement multiple factor authentication (MFA) and authorization mechanisms, which leverage something you have, something you know, or something you are.
Nearshore vs. Offshore: Navigating the Hidden Hassles of Outsourcing to Asia

Examples of MFA include biometric verification, smart card authentication, and token-based authentication.
2. Least Privilege Access
Zero Trust security policies limit access to network resources to only what is necessary for each user and device to perform their specific job functions. By adopting the principle of least privilege, organizations can minimize the potential damage caused by a compromised user account or device.
3. Assume Breach
The “assume breach” principle of Zero Trust strategy acknowledges that no security system is infallible, and organizations should proactively monitor and detect potential security threats. This increases visibility into the network, enabling early detection of suspicious activities or unauthorized access requests or attempts.
4. Micro-Segmentation
The micro-segmentation principle of Zero Trust security involves breaking up the network into smaller sections or segments, limiting the potential impact of a security breach. Each segment contains a specific set of resources and has strict access control and policies in place. Through Zero Trust architecture, organizations can restrict traffic flow between different parts of the network, preventing lateral movement by attackers and containing potential breaches within a limited area.
5. Data Encryption
Zero Trust calls for organizations to protect data on devices, applications, and networks by using encryption to safeguard information both in transit and at rest. This ensures that even if unauthorized access occurs, the data remains unintelligible and unusable to attackers. Robust encryption algorithms and key management practices are essential to maintain the confidentiality and integrity of sensitive data.
Advantages of Adopting Zero Trust
The advantages of adopting Zero Trust for your organization’s cybersecurity are numerous.
- Enhanced Security: Zero Trust reduces the attack surface, minimizes the potential impact of a breach, and provides continuous verification, leading to a more robust security posture. Organizations that don’t deploy Zero Trust incur an average of $1 million in greater breach costs compared to those that do deploy, the Cost of a Data Breach report found.
- Improved Risk Management: 90% of IT and security leaders surveyed in Foundry’s 2022 Security Priorities Study said their organization is falling short in addressing cyber risks. A Zero Trust network enables organizations to better identify and mitigate potential security risks through strict access controls, least privilege access, and continuous monitoring, enhancing risk management capabilities.
Zero Trust also enables early detection of suspicious activities, facilitating swift response and minimizing potential damage. - Protection of Sensitive Data: Through data encryption and segmentation, Zero Trust helps safeguard sensitive data both in transit and at rest, ensuring confidentiality and integrity.
- Adaptive to Modern IT Environment: Zero Trust aligns with the evolving IT landscape, accommodating remote work, cloud services, and mobile devices, providing security regardless of the user’s location or device.
- Aligned to Compliance and Regulatory Requirements: Zero Trust principles align with many regulatory requirements, facilitating compliance efforts and ensuring adherence to industry-specific security standards.
- Business Continuity: Zero Trust mitigates the impact of security incidents, reducing downtime, and enabling faster recovery, ensuring continuity of operations.
The Zero Trust model, therefore, offers several tools to organizations to effectively combat the evolving cybersecurity threats in today’s digital landscape.
However, Zero Trust implementation presents a learning curve for organizations and, as with most new technologies, can prove to be challenging in the initial phase of adoption. Major pain points can include having to replace legacy systems that lack interoperability and the security features necessary for Zero Trust, which can be time-consuming and costly in the short term.
User experience can also be impacted by the additional authentication measures required by Zero Trust, so care should be taken to balance security and usability to ensure that productivity or user access and friendliness is not affected.
Zero Trust might also necessitate a cultural shift within the company as employees, previously accustomed to more permissive access controls, learn to move away from the traditional mindset of trust within the network perimeter.
Most importantly, Zero Trust requires skilled cybersecurity professionals and dedicated resources to implement and maintain the complex security infrastructure. This can prove to be daunting and expensive, particularly for small and medium businesses. A trusted service provider with deep cyber security expertise and capabilities can be an effective partner for implementing and maintaining the Zero Trust architecture for your business, securing it against the growing threat landscape.